I follow three guiding principles when selecting which software to use:
- Privacy – Does the software (and vendor) value and guard my privacy?
- Data Longevity – What happens to my data if the vendor goes out of business? Or the vendor discontinues the tool?
- Vendor lock-in – how easily can I export my data and then import it into a different tool? Am I trapped within a single vendor’s ecosystem?
This article focuses on why I believe these principles are important when choosing software. But these principles also apply to many other purchasing decisions we make. Buying a car, a TV or even a lawn irrigation controller? You should consider these three key principles before making your choice.
Privacy
With today’s continual stream of data breaches, it is pretty much guaranteed that any information you put on the internet will end up in the hands of hackers. When you put information on the internet, you are trusting the keeper of your data to safeguard it. History shows that many vendors do a lousy job protecting your data.
Vendors can use encryption to protect information they store. But implementing encryption properly is hard, and many vendors fail.
Encryption uses keys to scramble and unscramble your data. Securely deriving and storing encryption keys is critical to keeping your data private.
Many vendors claim to encrypt your data both “in motion” (when it is moving across the internet) and “at rest” (when it is stored on a vendor’s computer). This is typically referred to as “End-to-end Encryption1”.
Protecting data in motion is a mostly solved problem. The “https” protocol encrypts transfers of web page contents. Email transfers are protected by similar encryption protocols. SSH encrypts sessions. DNS queries2 however, are not encrypted. Because your Internet Service Provider (ISP) can see your unencrypted DNS queries, they are able to create a list of all websites that you visit3.
Many vendors claim to encrypt your data when it is stored at rest on their servers. But who holds the keys to your encrypted data - you or the vendor? In most cases, the vendor maintains the encryption keys, meaning that they can decrypt and access your data stored on their servers. And if those keys are stolen, then others can access your data as well.
By now, you are probably thinking that the Retired Engineer is an old curmudgeon. Hmmm… probably true. But I am concerned that large companies are amassing tremendous amounts of information about you.
Examples:
- Google / Alphabet
- Has all your email if you have a Gmail account (but claims they stopped reading them starting in 20174)
- Knows everything you search for (if you use Google search)
- Knows every website you visit that uses Google Analytics (which almost every website uses)
- Knows that you enjoy watching “baby fashion show” videos on YouTube
- Has all your documents if you use Google Docs and Google Drive
- Knows where you have been if you use Google Maps
- Knows who you call and text if you use an Android phone or Google Fi
- Amazon
- Knows everything you bought from them in the past 29 years (check out your Amazon purchase history – Retired Engineer’s starts in 1997!)
- Knows where you live and has your credit card numbers
- Knows what you like to watch (via Prime Video)
- Knows what music you like (via Prime Music)
- Knows which medicines you take (via Amazon Pharmacy)
- Knows what you eat (via Whole Foods)
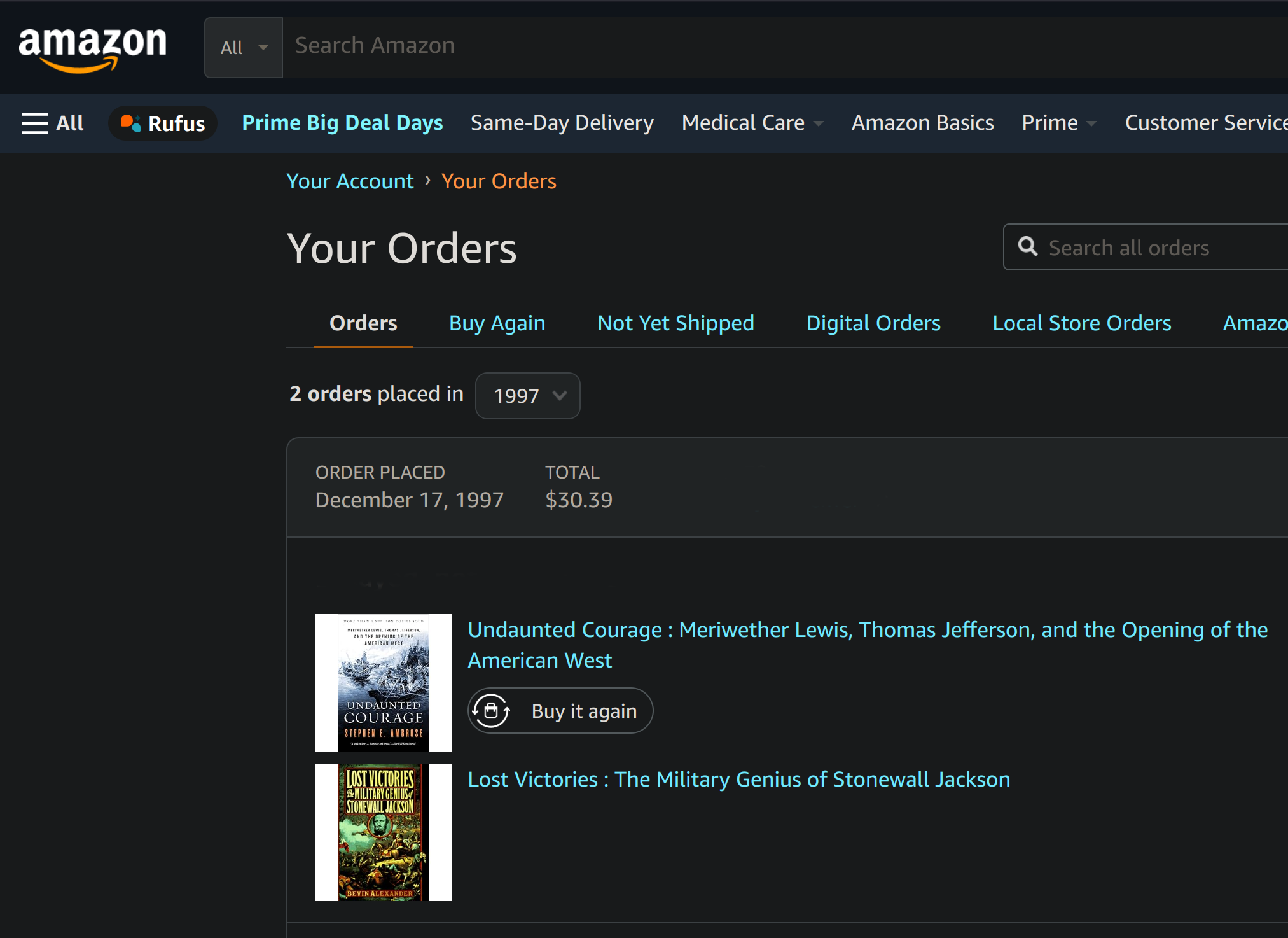
When Amazon Sold Only Books
- Meta
- Knows everything you share with your friends (via Facebook)
- Has all your photos (Via Instagram)
Do you trust these vendors to keep private all this information you entrust to them?
Suggestions for enhancing your privacy
- Avoid using products where companies have the ability to read your data (even if their privacy policies say that they won’t).
- Avoid using products that encrypt your data, but retain the ability to read it (i.e. product where the vendor retains the encryption keys).
- Adopt a “Zero Trust5” policy when managing your data.
- Use open source products since their source code can be examined for privacy issues and security vulnerabilities.
A final thought on privacy: Why would a for-profit company offer a service for free? How do they make money from this? Probably by selling advertising. But how do they maximize profit from advertising? By selling targeted ads. And how do they know what ads to target you with? By collecting information on you and using that info to target you with ads they think you will respond to. When a service is free, the company is making money by using or selling your private data.
Longevity
Data File Formats
Microsoft Word 1.0 for MS-DOS was released in 1983. The first version of Word for Windows was released in 1989. WinWord 6.0 (the first widely used version of Word) was released in 19916.
Can you still read the ancient files that you created with Word 1.0 in 1983? How about files you created with WinWord 6 in 1993?
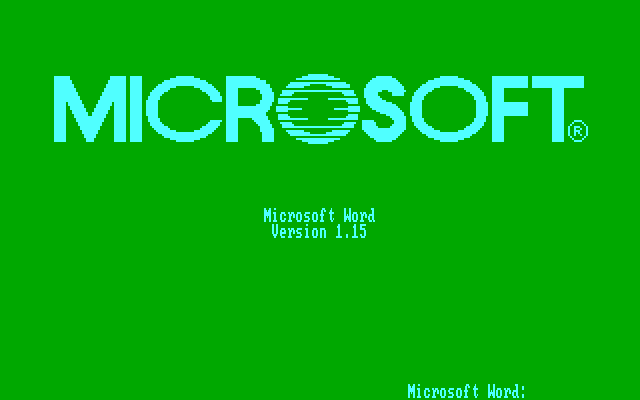
Microsoft Word 1.15 Splash Screen
The answer is probably “no”. Meaning that data created with WinWord 6 in 1993 may be lost forever. Why? Because old versions of Word used a binary format that was readable by that old version of Word but not by humans. This means that those files are “locked-in” – they cannot be used except by the vendor’s software.
The relentless progress of technology results in obsolete files that can no longer be read – lost data. And to be fair, not even Bill Gates was thinking about data longevity in 1983. But 40 years into the personal computer age, data longevity has become a serious issue.
It is impossible to avoid obsolete file formats entirely. Migrating data forward to newer formats every few years is a necessity. But it is also time consuming and expensive. When will you get around to converting your pile of VHS tapes to a more modern format? Probably never.
Here is how I mitigate the risk of obsolete file formats:
- Use simple human-readable formats, such as ASCII text files, when possible
- Use file formats that already have longevity, such as JPEG (for images), mp3 (for music), and mp4 (for video)
- Use open source formats rather than vendor-proprietary formats
Software Tool Obsolescence
Microsoft Word has lived for 40 years, and may live for another 40. Most software programs have a much shorter life. Vendors tend to obsolete software that doesn’t sell well or that has been overtaken by competitors.
Other vendors seem to take the approach of “throw the spaghetti at the wall and see if it sticks”. Google is notorious for starting projects then canceling them a few months or years later. See Killed By Google which as of October 2024 lists 296 different products that Google has killed.
How to mitigate the risk of obsolete software:
- Widely used software is less likely to go obsolete. Use software with a long history (like Microsoft Word).
- Use open source software. Even if it becomes unsupported by the original developer, others often pick up the project and move it forward (or fork it to start a new project)
- Avoid software from companies with a reputation for shutting down projects (I avoid using Google products when possible because I don’t want to waste time learning their software only to have them shut it down)
Link Obsolescence
When writing this blog, I link to informative articles on other websites. Doing this benefits my readers. But it also creates longevity issues. All links are valid when I create a post. But will they still be valid in a month, or a year, or ten years? I don’t control the websites I’m linking to, so it is inevitable that links on this blog will break.
Ideas I’m considering to mitigate this:
- Put all links I don’t control in a References section rather than within the main text. This will isolate potential problems to a single portion of the file.
- Put links in footnotes instead of within the main text.
- Use “link crawling” software periodically to find broken links.
- Only link to major websites (ones likely to still be online five years from now).
- Learn which websites change links often.
Vendor Lock In
Software vendors want to marry you and live happily ever after. Once you do marry them by adopting their products, you may find it is very difficult to switch to another vendor’s product.

Help! I'm Locked In!
Apple has often been accused of creating a “walled garden”. Apple’s ecosystem is beautiful when you are inside, but is very difficult to leave.
Let’s look at a few examples of vendor lock-in from Apple:
- Blue bubbles when messaging other iPhones, but green bubbles and degraded features when messaging Android
- Just released a new password manager that can only be used on Apple products and has no web version
- Photos taken on iPhone are in HEIC format rather than JPEG (will HEIC still be around in 30 years?)
- Sold copy-protected music readable only by Apple iTunes
- Apps for iPhone can only be purchased from Apple’s App store (Apple gets a cut of each sale)
- New Macs use proprietary Apple-designed processor and thus only run Apple’s MacOS7
- Exporting photos from iCloud is challenging
- iPhone / iPad used proprietary Lightning connector rather than USB-C
- Apple News+ allows you to save news articles that you like, but you can’t export the list or the saved articles themselves
To Apple’s credit, they try to move the market forward by adopting new technologies before others. They were the first company to get rid of floppy disks, first to have a CD-ROM, etc. Many times the industry follows Apple (i.e. Android copied the iPhone) but other times the industry goes a different way – then Apple users are stuck with proprietary (and eventually obsolete) technology. What should I do with all my obsolete Lightning cables? I’ll keep them together with my even more obsolete 30-pin Apple dock connector cables. (Retired Engineer still has a collection of RS-232 cables stashed in the basement!)
How to avoid vendor lock-in:
- Use software that supports portable formats (i.e. formats that can be opened by multiple vendor’s programs). For example, almost all Word Processing software available today can open MS Word files. As a result, using Microsoft Word formatted files (.docx) does not result in vendor lock-in.
- The software you are using almost certainly has an “Import” feature. But does it have an “Export” feature?
- Use open source software. When the source code is freely available, there is no vendor lock-in
Open Source Software
A common theme throughout this article is that open source software (OSS) mitigates privacy concerns, and helps with data longevity and avoiding vendor lock-in. I use open source software whenever possible. I’m not an OSS idealist that thinks all software should be free. Rather, I use it because I care about my privacy, and don’t want to be locked into a single vendor’s ecosystem.
Other Applications
Before concluding this article, let’s briefly consider how the principles of privacy, longevity and vendor lock-in apply to other products such as cars, TVs, and irrigation controllers.
Cars
- Modern cars are computer’s with wheels, and thus will have security holes.
- Do you have keyless entry or remote start? Can this be spoofed?
- Does your auto vendor track the location of your car?
- Some insurance companies give discounts if you let them install a device in your car that tracks your driving habits. Some rental cars also have this. Are you OK with giving up your privacy for an insurance premium discount?
TVs
- Modern TVs are a computer with a huge screen.
- Is your TV connected to the internet? If yes, what benefit do you get from this? (I have disconnected my TVs from the internet).
- Does your TV track what you watch? And does it “phone home” with this data?
- If you TV is connected to your home network, then it can potentially sniff your network’s traffic (remember the discussion earlier about unencrypted DNS?)
- If you watch a streaming service (Netflix, Amazon Prime, etc) using software built into your TV, then the TV vendor can potentially track what you stream. If instead you use an AppleTV or a Google Chromecast, then Apple or Google can track what you stream. Who do you trust – LG / Samsung / Sony or Apple or Google?
- See this article: https://arstechnica.com/gadgets/2024/10/streaming-industry-has-unprecedented-surveillance-manipulation-capabilities/
Irrigation Controller
- My irrigation controller is connected to the internet. The benefit I get from this is using my iPhone to control when my sprinklers run.
- It is connected to my home network and could potentially sniff my network’s traffic. To mitigate this vulnerability, I keep the irrigation controller and other “Internet of Things” (IOT) devices on a separate IOT VLAN isolated from my main network.
- It phones home regularly. (I plan to block it from doing this using my home DNS server but have not gotten around to this yet).
- It may stop working if the vendor shuts down the server it regularly connects to (potential longevity issue).
- Is there any way to install a security update? I have no idea. I have never installed an update. Does it update itself? I have no idea.
- All of the comments and questions above apply equally to wireless doorbells, Amazon Echos, WiFi-controllable electrical outlets and other IOT devices.
Conclusion
I value privacy, data longevity and avoiding vendor lock-in. I apply these principles both when selecting software and when purchasing other products.
I hope this article gave you some “food for thought” about your own choices. In a future blog post, I’ll discuss in detail the software that I use and why I selected it. Stay tuned!
-
DNS translates domain names such as amazon.com to the IP addresses that computers use to locate websites. ↩︎
-
Protocols are available that encrypt DNS traffic but they are not commonly used. See DNS over TLS and DNS over Https. ↩︎
-
https://www.wired.com/story/google-reading-personal-emails-privacy/ ↩︎
-
Apple’s new Macs do run Asahi Linux, which was painfully ported without support or assistance from Apple ↩︎